The Best Tips To Make Your Cover Letter Noticed
- Written by News Company
What is the best way to make your cover letter stand out when the hiring manager has dozens of them to look through? First of all, learn how to write a good one.
You might argue that no one is going to read it. And sometimes it’s true. But some hiring managers still expect to receive a cover letter. Pay attention if it is mentioned in the job posting. So, if they do read your cover letter, it will give you a chance to better pitch your candidacy to fill the position.
If you are going to send your cover letter, be sure to follow these steps to put all the odds on your side.
1 — Send it in email with the CV
These days, recruiters no longer expect to receive a formally-written business letter attached to your email. Make things simpler, and just type your cover letter content in the body of the email. Keep it short and sweet. Then attach your CV, and you are done. By doing so, you will make it easier for the recipient to read and digest your stuff quickly. Plus, if a hiring manager can open your email and immediately read about your skills without having to double-click on multiple attachments, then the chances increase that they will notice the words on the screen.
Furthermore, do not be afraid to reach out to a professional team of recruitment and CV writing experts like ARC Resumes if you would like to ensure that both your cover letter and CV are of the highest possible standard. If you would like to learn more about the different ways that ARC Resumes can help you to move on to the next stage of your career, you can find some useful resources on their website here: https://www.arcresumes.com/.
2 — Complement your cover letter with email signature
When looking for a job, it is crucial to use a professional email signature. If you design it properly, this may help you gain trust with your email readers and impress them.
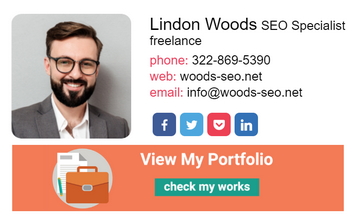
If you don’t know how to create your first free email signature, start by making one with an email signature generator and install it to your email client.
To help you further, we have added a few tips below so you can make your signature the most efficient.
Tip #1: In your title field, don’t mention that you are unemployed. Instead, it is better to list your skills (i.e., graphic designer).
Tip #2: Although optional, it is highly recommended to include your photo. By doing so, you are giving your email footer a more personal touch and remind the recipient that you are a real person on the other side of the computer screen.
Tip #3: If you have an online portfolio, personal blog, or website, consider including the link. With an email signature, it’s always easier to describe what you are linking to. For instance, hyperlink to a short description, such as “View My Portfolio,” “Go to Blog,” “My Infographic Resume,” and so on. Keep in mind that you can link to almost any other online source you want to draw attention to.
Tip #4: Provide easy access to your social media profiles (for most professionals it’s LinkedIn; and if you are, for example, a photographer, it would be appropriate to link to Pinterest). This way, you enable the recruiter to stay connected with you on both professional and social levels. But make sure there is no incorporate engaging content in your profiles that can scare off a potential employer.
3 — Use text only
Since usually we don’t know what email provider the recruiter is using, so it is better to avoid adding any images or experimenting with formatting. The recipient may not see a formatted message the way that you intended. To be on the safe side, we recommend you stick to plain text.
For better readability, it is also better to avoid long paragraphs or a series of stacked, short sentences.
4 — Mention what you like in a specific company/position
Use your cover letter to show the recruiter that you have done your homework and see you as the perfect fit for the company. You can also mention that you are interested in some specific projects the company does, a product they recently released, and so on.
Tip: Using the recruiter’s name shows you did your research. And you increase your chances of being noticed.
5 — Be cheerful but professional
Be professional, but don’t overuse the industry language to demonstrate your knowledge. Try to balance a professional but friendly, cheerful tone throughout the letter.
Tip: Stay away from such annoying phrases as “heavy lifting,” “think outside the box,”’ “game-changer,” “exceptional communicator,” “problem solver.”
6 — Check multiple times for errors
Although this seems obvious, many job seekers tend to forget to check their cover letters for typos, misspelled names, and other grammatical errors. It is better to do it at least once. Twice or even three times can be even better.
If you don’t consider yourself a grammar expert or don’t always know when you have made a mistake, ask a trusted colleague or a friend to read your CV and cover letter before you send it.
Further, you can send it to yourself to be sure the formatting is perfect. Proofread it one more time. Send.
What not to include in your cover letter?
If you want your cover letter to stand out only in a good way, keep in mind a few things you shouldn’t include in your email if you want to make a positive first impression:
- It’s not necessary to include too much personal information. Better keep the focus on your qualifications for the job.
- Avoid including salary requirements unless the job posting requires that you do. Even then, think twice before you respond. By asking too much money, you can easily knock yourself out of contention for the job. On the other hand, you are risking to get an offer for less than you deserve.
- Never mention how you quit your last job, especially if you were fired.
Conclusion
Even if it’s not required by the employer, a compelling, well-written cover letter gives you the opportunity to sell your professional and personal skills to the company and demonstrate to them why you would be a great fit for the job. Now that we shared our best tips, you can give your cover letter an amazing shape and land your dream job very shortly. Good luck!
Description: Use these six simple tips to make your cover letter stand out.








