Australia is under sustained cyber attack, warns the government. What's going on, and what should businesses do?
- Written by Mahmoud Elkhodr, Lecturer in Information and Communication Technologies, CQUniversity Australia
Prime Minister Scott Morrison had some alarming news for Australians this morning: we are under cyber attack. He informed the nation the attacks “hadn’t just started”, and that Australian businesses and governments are being widely targeted.
It is unclear why the government chose today to make the announcement, or indeed what exactly is going on.
The attack is described as “state-sponsored”, which means a foreign government is believed to be behind it. When asked who that might be, Morrison said there is a high threshold for drawing that kind of conclusion, but added:
…there are not a large number of state-based actors that can engage in this type of activity.
This has been interpreted as a coded reference to China, which the Australian government reportedly suspects of being behind the attacks.
Read more: Why international law is failing to keep pace with technology in preventing cyber attacks
What do we know about the attack so far?
An advisory note posted on the government’s Australian Cyber Security Centre website describes the attack as a “cyber campaign targeting Australian networks”.
The advisory says the attackers are primarily using “remote code execution vulnerability” to target Australian networks and systems. Remote code execution is a common type of cyber attack in which an attacker attempts to insert their own software codes into a vulnerable system such as a server or database.
The attackers would not only try to steal information but also attempt to run malicious codes that could damage or disable the systems under attack.
Detecting this is hard, and would require advanced defensive measures such as penetration testing, in which trained security professionals known as “ethical hackers” try to hack into a system in an attempt to find potential vulnerabilities.
What systems have been affected?
The advisory linked the attack to three specific vulnerabilities in particular systems, detailed in the table below. Any business that uses any of these systems is vulnerable to attack. It is too early to tell whether other systems are also vulnerable; other vulnerabilities may emerge as investigations continue.
|
Affected system |
Description |
Action required |
|
Microsoft Internet Information Services (IIS) |
This is a general-purpose webserver from Microsoft that runs on Windows systems. The most common use of an IIS is to host web-based applications and simple static websites. |
For all three systems:
|
|
SharePoint |
A SharePoint Server is used by organisations to manage Office 365 Enterprise accounts within their own organisation. |
|
|
Citrix |
The affected Citrix products are mainly Citrix gateways and servers. These are used to support web, cloud and mobile application services. |
How can businesses protect themselves?
Even though the specific threats are not fully known to the public, there is a range of measures businesses can take in the meantime. These include:
Use available government resources
The federal government has provided extensive cyber safety guidelines for Australian businesses, featuring advice on cyber security and data protection, and information on the various types of cyber threat.
More comprehensive cyber security guidelines can be found at the ACSC website, including detailed advice on secure management of databases, email systems and physical computer assets, among others.
Watch out for spam
Phishing is not just limited to email. These scams can be executed via text messages, social media such as Facebook, and VOIP messaging services such as WhatsApp.
As a general guide:
do not open messages or attachments from unknown senders
remember that genuine organisations such as banks, government departments and online retailers never ask for personal information via email, and you should always check with them directly (such as by calling them) if in doubt.
Read more: Everyone falls for fake emails: lessons from cybersecurity summer school
Beware DDoS attacks
A “distributed denial of service” (DDoS) attack is the most common type of cyber attack. It works by flooding your website with traffic, preventing genuine customers from reaching your website. Think of it like a traffic jam clogging up a highway and preventing cars from reaching their destinations.
Luckily, there are ways to reduce the impact of DDoS attacks, such as by using intrusion detection and prevention systems. If you are concerned about DoS attacks speak with your internet provider about developing a DDoS response plan.
Have a backup plan
A “continuity plan” ensures important assets such as personnel records, customer databases and network configurations are protected and can be restored quickly in the event of a cyberattack.
Suggested plans are available via the federal and Queensland governments.
Businesses should also follow sensible IT security procedures, which include the following:
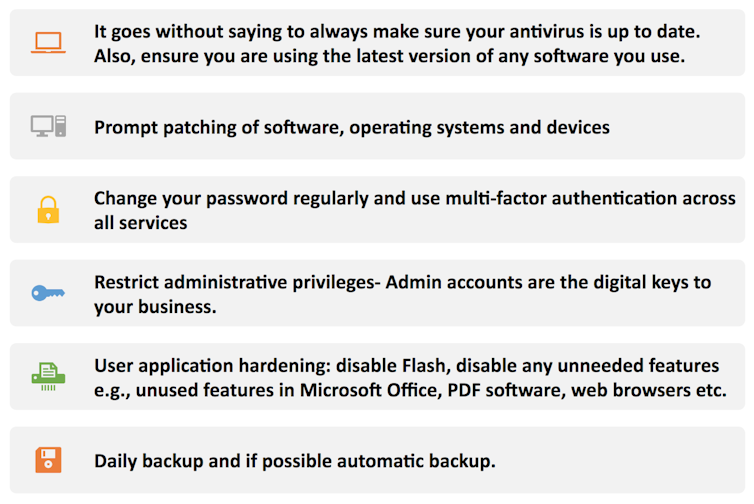 What businesses should be doing to minimise their cyber security risks.
Mahmoud Elkhodr, Author provided
What businesses should be doing to minimise their cyber security risks.
Mahmoud Elkhodr, Author provided
Regardless of the details, the latest announcement is a reminder that we should not lower our guard against cyber attacks. The latest round of cyber attacks are likely the result of previous “reconnaissance attacks”, which revealed existing vulnerabilities in Australian networks.
Taking the steps outlined above could help prevent hackers mounting similar attacks in the future.
Authors: Mahmoud Elkhodr, Lecturer in Information and Communication Technologies, CQUniversity Australia





